Developer Roundtable - Click-Jacking
In the wonderful words of Cody Brooks: “Did not will do, but now will did”
In this week’s Developer Roundtable, we dove into the topic of questionable emails and effective response strategies. In particular, the Flagrant email received a notification concerning a potential vulnerability to click-jacking on a website we are actively developing. Is this notification accurate? Possibly. Is it a legit source? Probably not.
What even is click-jacking and why is it important to prevent? Well, click-jacking is when an attacker layers over a legit website with their own buttons or links. The idea is that when a user goes to click the “legit” website button or link, instead they are clicking the attackers button or link. This allows the attacker to send the user to a different website which is most likely owned by the attacker. If you want examples, here are several for click-jacking.
As a team, we discussed the unusual nature of the email we received and suspect that its motivation may be malicious. We concluded that the best approach is to disregard the email while conducting an investigation into potential vulnerabilities on the targeted website. Our priority is to enhance the defense against click-jacking attacks. But how?
OWASP is a valuable resource that provides free and open resources for web application security. In this article, they offer several methods to test for click-jacking vulnerabilities. Additionally, Jim recommended an application called ZAP and we tested the site as a group using ZAP.
ZAP, short for the OWASP Zed Attack Proxy, is a powerful open-source security tool designed for testing web applications for vulnerabilities. It can help identify and mitigate security issues such as cross-site scripting (XSS), SQL injection, and more. To use ZAP, you can simply download and install it, then configure it to intercept and analyze web traffic. ZAP provides various features for scanning, spidering, and reporting on security vulnerabilities within web applications, making it an essential tool for web developers and security professionals. Here is what the interface looks like:
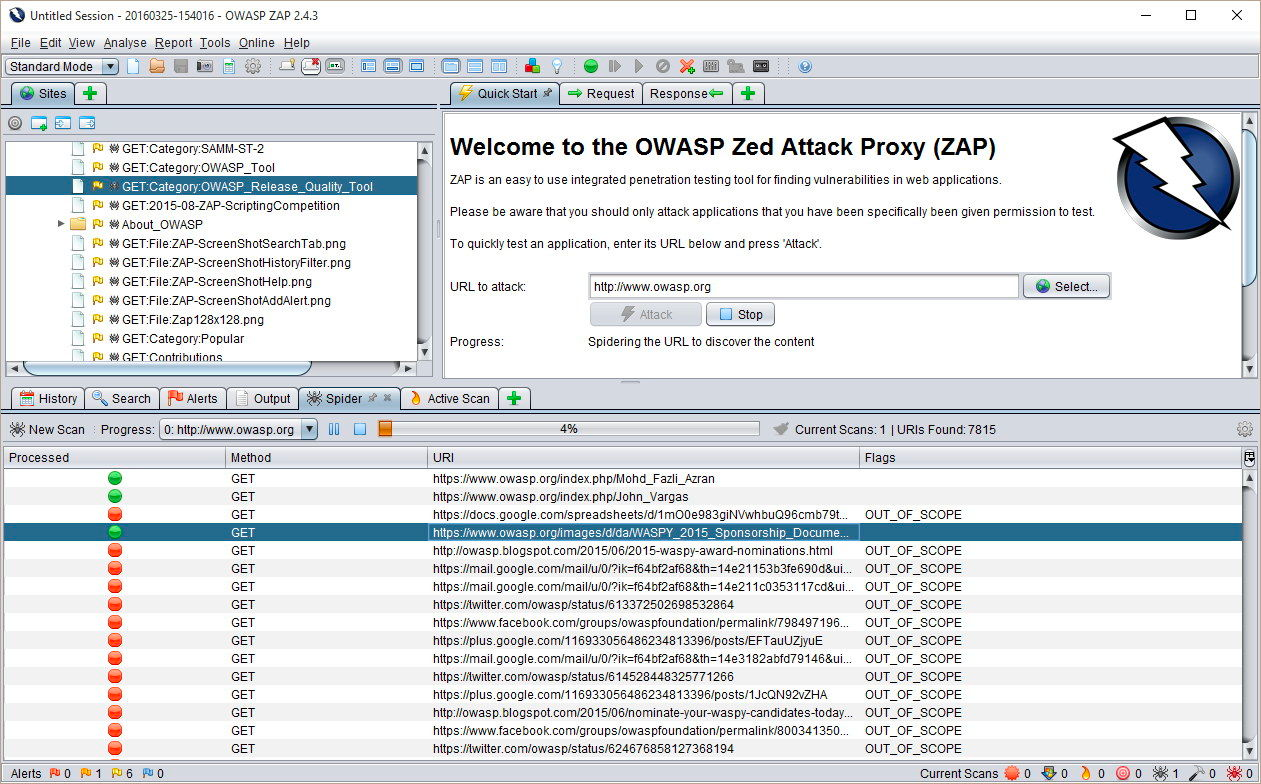
It was pretty awesome to see the vulnerabilities of the site and test them out together. We ended up finding a solution for the site and re-tested to find out that the vulnerabilities were covered. So, what might have started as a sketchy email ended up becoming a learning moment as a group and a better protected website.
Enjoyed this content? Join our developer roundtable, we meet every other Friday from 10:30 - 11:30 am CT. Hope to see you there!
If you’re looking for a team to help you discover the right thing to build and help you build it, get in touch.
Published on September 24, 2025
